- Print
- DarkLight
- PDF
Configuring Single Sign-On/SAML
- Print
- DarkLight
- PDF
RIMS supports Security Assertion Markup Language v2 (SAMLv2), an open standard protocol for Single Sign On. This allows lending institutions on the RIMS platform to manage their users and those users' identities within the institution's system. With SAML, selected data can be sent to automatically log users into RIMS.
For more information about enabling and configuring SAML for your institution, please contact RIMS Customer Support at support@exactbid.com or 866-319-7467.
RIMS SAML Implementation
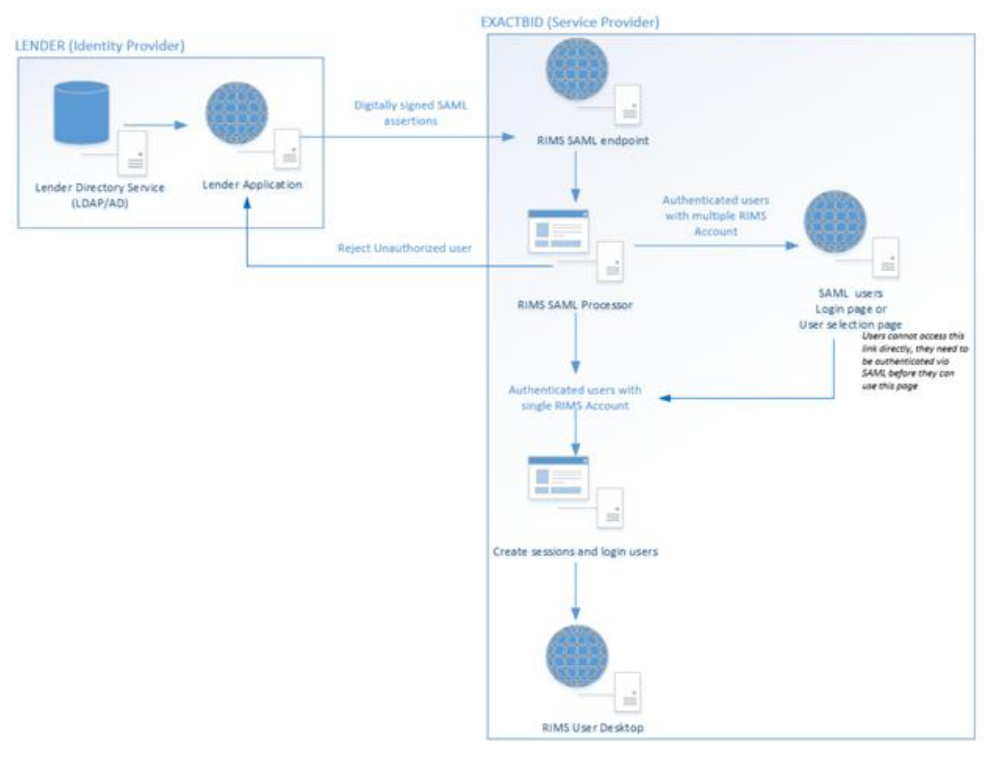
SAML exchanges digitally-signed XML documents (SAML assertions) between system entities referred to as an Identity Provider and a Service Provider to authenticate a User.
Identity Provider (IdP)
An Identity Provider is the source application or database where lenders manage their users' accounts and roles. This is also where the user will manually log in. The Identity Provider makes SAML assertions about the identity of the user.
Service Provider (SP)
ExactBid is the Service Provider and it uses the SAML assertions it receives from the Identity Provider to verify and translate the data to a RIMS session by either looking up the user or creating a new account. Once found, it automatically logs that user into the application.
SAML Setup
1. SAML Certificate fingerprint
Lender to provide the certificate to be used as fingerprint for each SAML request. Identity Provider will use this certificate to digitally sign the SAML document before sending it to the Service Provider. ExactBid will then use this same certificate to validate the authenticity of each SAML request received. Please provide contact information for a member of your Domain Trust Management team so that IT representatives of both organizations can work directly to get SAML configuration requirements identified and set up for a timely deployment of RIMS within your organization.
2. SAML Assertions (Fields)
Lender needs to select a field or a combination of fields in the list below that will match a unique identity of the user. IdP will include these data points in their SAML assertions and SP will look up those values within the RIMS database and create a user session based on the RIMS account found in the system. In cases where IdP account is associated to multiple RIMS users, there is an option to either show the user a list of accounts found on RIMS or let the user login to RIMS (see number #4).
At least one of the fields below must be required.
| Field Name | Required | Notes | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
No (Unless Auto-Create On, then Yes) | |||||||||||||||||
Import User ID/External User ID (SAML "NameID") | Yes (Always) | This is a text field within RIMS system that the lender can use to store another unique identifier of the user. Typically, this is the user code within the lender’s internal system. | |||||||||||||||
| Role | No (Unless Auto-Create On, then Yes) | Values are either User Type IDs or User Type name. Role values:
| |||||||||||||||
| First Name | No (Unless Auto-Create On, then Yes) | ||||||||||||||||
| Last Name | No (Unless Auto-Create On, then Yes) | ||||||||||||||||
| Address | No | ||||||||||||||||
| City | No (Unless Auto-Create On, then Yes, unless SAMLRequiredFields set) | ||||||||||||||||
| State | No (Unless Auto-Create On, then Yes, unless SAMLRequiredFields set) | ||||||||||||||||
| Zip | No (Unless Auto-Create On, then Yes, unless SAMLRequiredFields set) | ||||||||||||||||
| Phone Number | No |
3. Remote login and logout URL
This is the URL within the lender’s system; RIMS will use this link to redirect the user if they try to login directly within RIMS. Users will be redirected to the logout URL when they click the Logout button in RIMS.
4. One to many User
Lender uses this option if they want to allow multiple RIMS User accounts to be associated with one account in their system. If the lender chooses to enable this, they have two options to handle how a user chooses to login to RIMS.
a. Login
If the user attempts to authenticate via SAML, and the authentication information matches more than one RIMS user account, then the user is presented with a normal RIMS login screen asking for a username and password. The only difference is that there is a message near the username/password boxes indicating that multiple accounts have been found and they need to log in manually.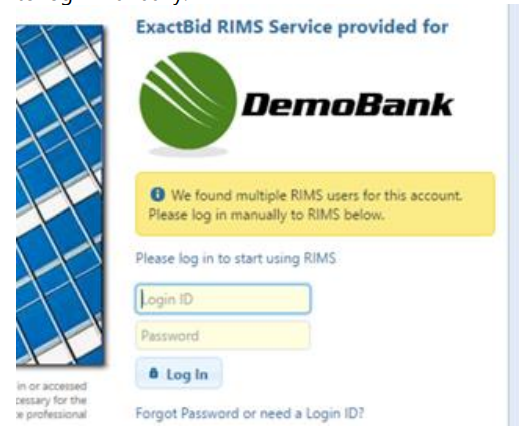
b. User picker
If the user attempts to authenticate via SAML, and the authentication information matches more than one RIMS user account, instead of asking for a username and password the system presents a list of the matching accounts to choose from. User just needs to select from the list without having to enter any username or password.
5. Auto-create
If a user logs in via SAML and RIMS cannot find the user within the system, it will automatically create the user using the information as specified in #2 within the SAML document. This setting is optional.
6. Auto-update
If a user logs in via SAML and RIMS finds the user within the system, it compares the information from the SAML document to the RIMS account found. If the RIMS information does not match, the system will overwrite RIMS data with what is in the SAML document. This setting is optional.
SAML Customer Setup Checklist
The table below is populated with the default configuration.
| Customer | Demo Bank | ||||||||||||||||||||||
| SAML Certificate fingerprint | Sent to ExactBid on MM/DD/YYYY | ||||||||||||||||||||||
| Fields |
| ||||||||||||||||||||||
| Remote Login URL | |||||||||||||||||||||||
| Remote Logout URL | |||||||||||||||||||||||
| One to Many user? | No | ||||||||||||||||||||||
| Login | N/A | ||||||||||||||||||||||
| User picker | N/A | ||||||||||||||||||||||
| Auto-create | N/A | ||||||||||||||||||||||
| Auto-update | N/A |
.png)
